Amazon GuardDuty: Mastering Threat Detection and AWS Security

Securing Your AWS Cloud Environment with Amazon GuardDuty
In today’s cloud-powered world, businesses of all sizes are migrating to AWS for its scalability, reliability, and vast array of services.
As enterprises collect and monitor large amounts of log data across their cloud accounts and workloads securing their AWS/Cloud environment is paramount. Managing security in a cloud environment can be a daunting task. Breaches and data leaks are constant threats. All in all, how can businesses secure their cloud environment against cyber threats and ensure reliability and scalability without disruptions?
Here’s where Amazon GuardDuty steps in – a powerful threat detection service that safeguards your valuable data and resources.
What is Threat Detection?
Every business with sensitive information is at risk of cyber threats, no matter its size, industry, or security level. As hackers get smarter and new threats like ransomware emerge, businesses must use tools that constantly watch for potential problems. These tools give alerts if anything suspicious is happening. Without them, businesses can’t catch and stop threats before they cause harm. Detecting unusual behavior early is the key to stopping attacks and responding quickly to keep things safe.
Finding threats in AWS log data is challenging because there’s a lot of information to go through. That’s where tools for threat detection come in handy. Instead of having the IT team do the work manually, security services like Amazon GuardDuty can always keep an eye on the log data.
What is AWS GuardDuty?
AWS GuardDuty is a security service that detects threats and helps you secure your AWS environment.
An intelligent threat detection service that continuously monitors your AWS accounts for suspicious activity. Leverages machine learning (ML) to identify anomalies and potential security breaches. Integrates with AWS threat intelligence feeds to stay updated on the latest cyber threats.

The good thing about Amazon GuardDuty is that it is highly automated. It finds threats with Machine Learning, anomaly detection, and 3rd party data. It builds patterns that find potential security issues.
Note that GuardDuty doesn’t prevent issues, but only detects them. That’s why GuardDuty alone won’t protect you from issues like DDoS attacks. But you can pair GuardDuty with AWS Shield for maximum security.
Top 5 Reasons Why You Need AWS GuardDuty:
- Early Threat Detection: Be proactive! Amazon GuardDuty identifies potential threats before they escalate into major security incidents.
- Reduced Risk: GuardDuty minimizes the risk of data breaches, unauthorized access, and other security nightmares.
- Simplified Security Management: Free up your IT team’s time! AWS GuardDuty automates threat detection and analysis, letting your team focus on higher-level tasks.
- Enhanced Security Posture: GuardDuty strengthens your overall security posture in the AWS cloud.
- Continuous Monitoring & Peace of Mind: GuardDuty constantly monitors your AWS environment, giving you peace of mind.
What Logs Does GuardDuty Track?
Some of the data sources are foundational, others are optional. Here are the main log sources that GuardDuty tracks. For all 3, GuardDuty starts monitoring automatically right after you enable the service.
- AWS CloudTrail logs capture API activity in an AWS account. GuardDuty helps find unauthorized access or compromised credentials.
VPC Flow logs show IP traffic going in and out of the Virtual Private Cloud network.
- DNS logs that turn domain names into IP addresses.
Additionally, GuardDuty can track logs within these AWS services:
- EKS protection includes audit log and runtime monitoring.
- Lambda network activity logs can show malicious code in Lambda functions.
- EBS volumes that are attached to EC2 are scanned for malware.
- RDS login activity shows access threats.
- S3 protection looks for security risks in API operations.
What are the key features of AWS GuardDuty?
- Monitors CloudTrail logs, VPC Flow logs, and DNS logs.
- Integrates with additional AWS services.
- Assign severity levels to findings.
- Sends automated notifications for threats.
What Happens When GuardDuty Finds a Threat
The diagram below clearly explains how AWS GuardDuty handles a threat.
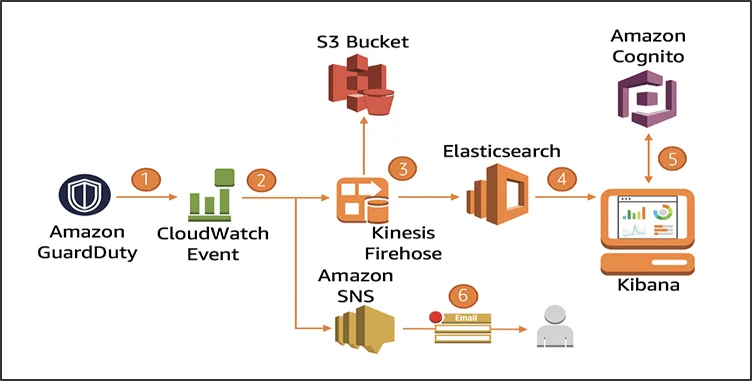
- GuardDuty findings are sent to CloudWatch Events within 5 minutes of detection.
- CloudWatch Events have two destinations: SNS and Firehose. You can apply Lambda functions to refine the findings.
- Firehose delivers data to S3 Buckets for long-term storage and to Elasticsearch for analysis.
- For visualization and operational insights, you can use Kibana, which is a built-in plugin for Elasticsearch.
- Authentication is handled through Cognito user pools.
- SNS will notify via email and SMS when GuardDuty identifies a threat.
AWS GuardDuty Capabilities:
- Detection of unusual behavior: GuardDuty keeps a close eye on any unauthorized attempts to get into your network, even if it’s through API calls. It watches out for anything strange, like logins from weird places, wrong use of passwords or sudden spike in traffic.
- Malware Detection: It keeps an eye on your network for harmful software, such as trojans and crypto miners. Essentially, it checks the EBS volumes connected to the EC2 instances and container workloads. Please note that scanning for malware costs extra – once the trial period ends, you’ll need to pay for EBS volume snapshots.
- Data Breaches: GuardDuty watches for signs of data breaches or irregular data transfer patterns in your AWS infrastructure. It’s vigilant for large or unexpected data transfers, unusual access patterns, or any activities that could indicate unauthorized movement or potential loss of data.
- Network Insecurities: GuardDuty monitors traffic for known malicious botnets or command-and-control servers. It flags suspicious DNS-related activities that might indicate data exfiltration.
How to get started with AWS GuardDuty?
Setting up amazon GuardDuty is straightforward! It requires minimal configuration and integrates seamlessly with your existing AWS environment.
- Visit the official AWS documentation for GuardDuty
By employing AWS GuardDuty, you gain a powerful threat detection shield for your AWS infrastructure. Its automated analysis, continuous monitoring, and advanced ML capabilities empower you to confidently navigate the cloud security landscape.
Ready to take your security to the next level?
Book a Consultation call with Altimetrik Practitioner and learn how we secure your AWS environment with best-in-class support.
Key Questions about AWS GuardDuty?
There are many security services within AWS which can lead us to many different security options. So, let’s figure out how amazon GuardDuty is standing tall from other security services.
- Security Hub aggregates findings from many AWS services including GuardDuty. When GuardDuty finds a threat, it may go to the Security Hub where it can get neutralized.
- Inspector focuses on vulnerabilities in AWS applications, while GuardDuty finds threats in event logs. In other words, GuardDuty looks at what happened, and the Inspector checks what can happen.
- Macie protects sensitive data in S3 buckets. It can also ensure compliance with regulations like HIPAA. Yet, Macie and GuardDuty serve different purposes, and they don’t directly integrate.
- Shield protects from DDoS attacks, while GuardDuty can add insights into the attacks to help Shield fight them. These services serve different purposes but can work together to fight DDoS.
- WAF is a firewall that monitors HTTP and HTTPS traffic. It prevents exploits like SQL injection and XSS in web apps. While GuardDuty works like an antivirus, WAF is an intelligent firewall.
- Trusted Advisor mainly helps to optimize costs and performance. But it also addresses the security gaps. It can ensure that you follow best practices and standards in security.
- SIEM looks over the entire network, while GuardDuty checks the entrance to it. While GuardDuty is not a SIEM, there are many different SIEM tools like Splunk or IBM QRadar.
GuardDuty and Machine Learning
GuardDuty uses machine learning to detect anomalies in the behavior of your account. So, when you first set up GuardDuty it takes between 7 and 14 days to set a baseline as it needs to establish what is normal behavior in your account. Once the baseline has been created, GuardDuty can then actively begin monitoring your account. When active, you will only see findings if GuardDuty detects behavior that it considers a threat.
Each GuardDuty finding has an assigned severity level (Low, Medium, and High) and value (0.1 to 8.9) that reflects the potential risk.
- “Low” (0.1 – 3.9) level indicates suspicious or malicious activity that was blocked before it compromised your resource.
- “Medium” (4 – 6.9) level indicates suspicious activity. For example, a large amount of traffic is being returned to a remote host that is hiding behind a network.
- “High” (7 – 8.9) level indicates that the resource in question (e.g. an EC2 instance or a set of IAM user credentials) is compromised and used for unauthorized purposes.
Also read: Enhancing Security in Amazon Web Services Cloud Environments
AWS GuardDuty Best Practices
GuardDuty is highly automated, hence it takes care of itself. There’s a straightforward setup guide mentioned in the reference section of this blog. It only takes a few minutes to enable all foundational services. We can fine-tune GuardDuty as well. This master class by Ryan Holland, Principal, Industry Specialist, AWS, and Nathan Case, Sr. Solutions Architect, AWS shares some handy GuardDuty tips. The link to the webinar is available in reference 2.
Here are some best practices, though:
- Link all the AWS accounts – If you have multiple accounts, set up a master member to centralize GuardDuty. You can use the multi-account script to speed up the process.
- Update your IP Address lists – Both trusted and threat lists. You can purchase threat feeds from third-party companies like CrowdStrike or generate your lists.
- Use filters to archive expected Findings – When you run a security assessment, you expect GuardDuty alerts. But you don’t have to clutter your findings list with them. Hide and archive them instead.
Conclusion
By leveraging the power of AWS GuardDuty, enterprises gain a robust threat detection solution that proactively safeguards AWS infrastructure. With its automated threat analysis, continuous monitoring, and advanced machine learning capabilities, along with seamless integration within the AWS environment, GuardDuty allows complete reliability and helps businesses focus on growth while taking care of security and scalability on the cloud.
References:
.svg)




.svg)